Hospitality
CLIENT: Exclusive Private-Members Club Private, single tenant building 2 floors below ground and 5 floors aboveStipulated by management and stakeholders, preserving traditional ambience suffusing the club — members feeling as if they were at home — and not impacting service marked the overarching expectations that influenced objectives for security and operations, as well as ensuing design of the integrated security system.
Classifying space within the club according to its intended function(s) and users, including common (all members), limited, (only select members), and staff, further shaped appropriate security objectives and guided effective placement, as well as selection, of security hardware.
Security Objectives
- Reduce opportunity for unauthorized access (intentional or unintentional) between back of house and front of house areas without impacting service
- Isolate overnight guest area from adjoining club, but granting access to authorized persons, without impacting service
- Reduce opportunity for theft at library and shops
- Ensure access within club reflects member privileges and staff roles and responsibilities
- Flexible configuration (days/times) of access control (doors/elevators) and vehicle barriers to support daily operations (business and non-business hours) and special events and to safeguard club appropriately in relation to credible threats, as they arise
 Construction Phase
Construction Phase  Official Artists Representation
Official Artists Representation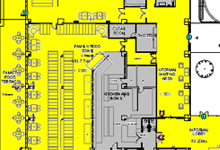 Floor plans
Floor plansOur key Operational Objective here was to integrate the access control and point of sales (POS) systems, enabling members to use their access cards for purchases at shops and restaurants, creating a “cashless environment."
Ed O’Reilly, Executive Director
Integrated function and components
- Access control
- Proximity readers: select doors and elevators
- Biometric (finger-scan) readers: server room
- CCTV
- Fixed cameras: parking lots, back of house, service entrances, day care entrance
- Intrusion detection
- Magnetic contacts installed on all perimeter doors
- Electronic article surveillance (EAS)
- Library and shops
- Vehicle barriers
- Rising bollards: main vehicle entrance
- Alarm monitoring
- On-site
- Point of sales (POS)
- Time and attendance (biometric finger-scan)
Data Centre
CLIENT:Global provider of co-location and data center services 7 floor data center owned by clientSenior management embraced that security has emerged a decisive factor for companies selecting a provider to entrust with their proprietary and critical information and telecommunications (ICT) functions.
Partitioning the data center into office, infrastructure, and server zones guided effective placement, as well as selection, of security hardware and development of role-based access control (RBAC) protocols.
Security Objectives
- Implement roll-based access control (RBAC)
- Staff granted access to zones according to operational requirements
- Client representatives granted access to zones on day/times contractually agreed upon
- Zone doors access-controlled—entry and exit—and alarmed to detect unauthorized access
- Elevators access-controlled to reduce opportunity for unauthorized access (intentional or unintentional) into server zones
- Zone doors, electrical riser panels, exterior fuel tanks alarmed to detect unauthorized access
- CCTV coverage and recording of exterior perimeter, zone doors, elevators
- Access and alarm reports (supported by linked video) for any combination of person, time, door
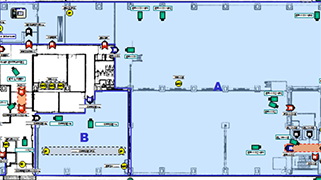 Construction Phase
Construction Phase 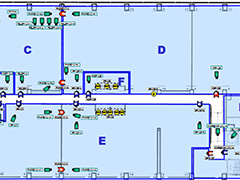 Official Artists Representation
Official Artists RepresentationIntegrated function and components
- Access control
- Zone doors and elevators access-controlled by PIN (scramble pad), proximity, or biometric (finger-scan) readers
- Interlocked portals (3) into office, infrastructure, and server zones configured “airlock style,” ensuring that one door is closed before another can be released
- Authenticate, using biometrics, identity of staff and client representatives before granting them entry into infrastructure and server zones
- CCTV
- Fixed and pan/tilt/zoom cameras
- Continuous recording of perimeter
- Event and alarm recording of zone doors and elevators
- Images stored for 30 days
- Intrusion Detection
- Magnetic contacts installed on zone doors, electrical risers, exterior fuel tanks
Luxury Residential
CLIENT: International real estate advisor that develops and manages commercial, residential, and mixed-use properties 5 floors featuring 17 luxury apartmentsWhen investing in a home, high net worth are influenced by feeling safe. Appropriate security safeguards their families and their property without diminishing the atmosphere of their home. The client acknowledged that offering appropriate security distinguishes luxury developers striving to attract and retain preferred high net worth residents.
Demarcating apartments and adjoining common areas shaped appropriate security objectives and guided effective placement, as well as selection, of security hardware.
Security Objectives
- Balance requirements for access control, intrusion detection, and CCTV with residents expectations of privacy, aesthetics, and convenience
- Role-based access control (RBAC)
- Residents granted access to apartments and common areas in accordance with their lease
- Building staff granted access in support of operational requirements
- Reduce opportunity for unauthorized access without inconveniencing residents
- Increase likelihood to deter and detect unauthorized access without inconveniencing residents
- From within apartments enable residents to
- Authenticate (image and voice) identity of guests and delivery persons
- Activate and deactivate apartment sensors and contacts
- Summon a security response immediately
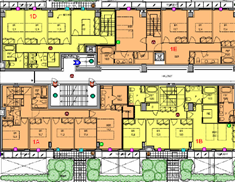 Construction Phase
Construction Phase 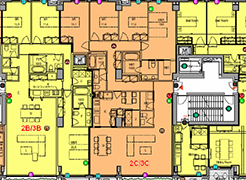 Floor plans
Floor plansIntegrated function and components
- Access control
- Readers (proximity) installed at garage door, building entrances, stairwells, and elevators
- Video intercom and door entry system installed within each apartment
- Alarm monitoring
- Building staff (on-site) and security company (off-site)
- CCTV
- Fixed cameras
- Continuous recording of perimeter
- Event and alarm recording of zone doors and elevators
- Images stored for 30 days
- Intrusion detection
- Glass break detectors affixed to balcony windows
- Lights activated by motion sensors, intended to deter intruders from entering apartments and to warn residents
- Contacts installed on sliding glass doors
- Local alarm will sound when forced entry is detected, intended to deter intruders from entering apartments and to warn residents
Banking & Finance
CLIENT: One of Asia’s leading Asset Management firms 3 full floors of a multi-tenant, Class A buildingConcurrent with fitting out its new global headquarters, senior management pledged to put into action a security program, underpinned by an integrated security system, equivalent, if not superior, to renowned global investment banks and financial services firms.
Classifying space within the office according to its intended users and function(s) and the information and infrastructure housed within, along with compliance considerations, guided effective placement, as well as selection, of security hardware.
Security Objectives
- Perimeter doors access-controlled to isolate office from contiguous public space
- Doors to sensitive rooms access controlled:
- Specific conference rooms, document center, and following departments: Audit, Human Resources, Corporate Planning, Investor and Public Relations, Trading and Fund Management
- Server rooms and UPS/hub/patch panel rooms
- CEO, CFO, CIO, and Legal Counsel offices
- Grant staff entry into office and sensitive rooms only on day/times in accordance with their job description and operational requirements: “role-based access control” (RBAC)
- Authenticate identity of staff before granting them entry into office and sensitive rooms
- Business hours: access card
- Non-business hours: biometric (finger-scan)
- Access and alarm reports (supported by linked video) for any combination of person, time, door
- CCTV recording of all persons entering and exiting office and sensitive rooms
- Scalability of access control and alarm monitoring
- Manage access and monitor alarms at global offices
- Common access card for global offices
 Floor plans
Floor plans Integrated function and components
- Access control
- Readers: proximity and proximity/biometric
- Biometric (finger-scan) readers: server room
- Intrusion detection
- Magnetic contacts installed on all access controlled doors
- Duress buttons installed at reception areas and CEO and CIO offices
- CCTV
- Fixed cameras
- Event and alarm recording of access-controlled doors
- Images stored for 30 days